
In today’s digital world, businesses of all sizes face a constant barrage of cyber threats. From sophisticated ransomware attacks to phishing scams, the risks are real, and the consequences are devastating.
With the average cost of a data breach at $4.88 million2, it’s never been more important for businesses to invest in IT security. Ignoring cyber threats could be a multimillion-dollar mistake that puts your customers, employees, and your bottom line at risk.
This IT Security guide covers everything you need to know about protecting your business from cyber threats and provides actionable strategies to keep your data secure.
Table of Contents:
- What Is IT Security?
- Cybersecurity vs. IT Security
- Types of IT Security
- Top IT Security Threats to Businesses
- Why is IT Security for Businesses So Important?
- FREE IT Security Consultation
What Is IT Security?

IT stands for “information technology.” IT security encompasses the strategies, tools, and systems used to protect an organization’s IT infrastructure from cyber threats.
A business’s IT infrastructure can include components like:
- Data: sensitive information pertaining to the business, employees, and customers
- Networks: internal and external communication systems, including Wi-Fi, LAN, and VPNs
- Devices: computers, smartphones, tablets, and other electronics connected to a network
- Software: the specialized computer programs, applications, and operating systems businesses rely on to operate
- Servers: physical and cloud-based computers that store and send data, programs, and software to other computers, over a network
- Peripherals: equipment connected to computers, including printers, scanners, and external drives
- Data Centers: a physical facility that stores and processes data for business
Most organizations’ daily operations depend almost entirely on their IT infrastructure, so having a solid IT security plan is vital.
The Main Objectives of IT Security
Although every business has its own unique infrastructure, all effective IT security strategies share these main objectives:
- Confidentiality: keep information accessible only to authorized users
- Integrity: ensure information remains accurate and unaltered
- Availability: keep information reliably accessible when needed (with minimal disruption during failures)
These objectives are often referred to as the CIA triad: confidentiality, integrity, and availability.
Cybersecurity vs. IT Security
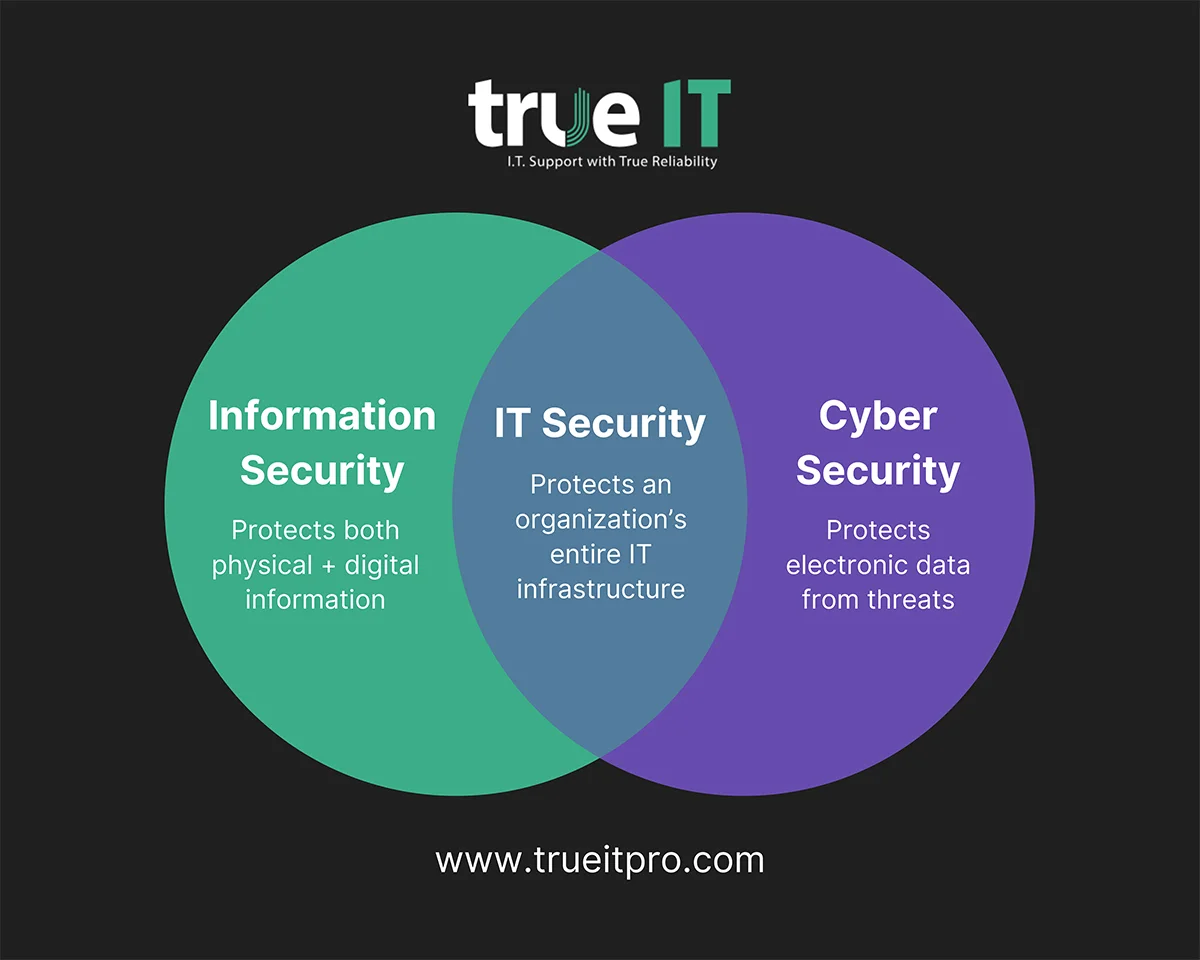
IT security is commonly confused with cybersecurity or information security (InfoSec). Although they share similarities, it’s important to understand how they differ:
- Information Security (InfoSec): Protects an organization’s information in all forms—physical (like printed documents), digital, and even spoken—by ensuring it stays private, accurate, and accessible only when needed.
- Cybersecurity: A subset of IT security that focuses on defending electronic data and systems from internet-based attacks like hacking, malware, ransomware, and phishing.
- IT Security: Bridges aspects of both InfoSec and cybersecurity to protect the entire IT infrastructure of an organization.
Both cybersecurity and IT security are considered subsets of information security. However, some organizations use the terms “cybersecurity” and “IT security” interchangeably since there is so much overlap.
Types of IT Security
There are multiple types of specialized IT security. Each type plays a critical role in a comprehensive IT security strategy, aiming to protect different aspects of an organization’s technology infrastructure.
Endpoint Security

An endpoint is any device that is connected to your organization’s network. This includes desktop computers, laptops, tablets, smartphones, and more. Just one vulnerable device could be an entry point for a cybercriminal to access sensitive data or spread malware throughout your entire network.
Common endpoint security strategies include:
- Antivirus Software: detects and stops malware when it attempts to breach an endpoint
- Device Encryption: locking devices with passcodes to prevent unauthorized access
Network Security
A network is a system that connects multiple devices, such as computers, servers, smartphones, or other hardware, to share information and resources. Network security protects your organization’s networks from unauthorized access, misuse, or cyber-attacks.
The goal is to keep the communication between devices and systems private and secure.
Common network security tools and strategies include:
- Firewalls: security systems that regulate incoming and outgoing traffic for a private network
- Intrusion detection systems (IDS): software that monitors a private network for malicious or suspicious activity
- Virtual private networks (VPNs): a secure, private network that encrypts data and masks IP addresses to protect users
Cloud Security

Cloud security protects all the information your organization stores in the cloud—which are remote servers hosted on the internet instead of local devices. Common examples of cloud-based software include Microsoft 365, Salesforce, and Google Cloud.
Common cloud security measures include:
- Cloud monitoring: continuously monitoring and evaluating the health of cloud-based IT infrastructure to ensure everything is running smoothly and securely
- Data backup and recovery: regularly backing up data stored in the cloud so it can be quickly restored after loss or an attack
Application Security (AppSec)
Most businesses rely on various programs, software, and other specialized applications to operate each day. Application security (AppSec) safeguards your organization’s software against unauthorized access to minimize disruptions and keep things running smoothly.
Some examples of application security measures include:
- Authentication: multi-factor authentication, biometrics (e.g. facial recognition), login information, or other measures that verify user identity before they can access the application
- Encryption: protects sensitive data within applications by converting it into unreadable code that is only accessible to those with a decryption key
- Patch Management: ensures all software and applications are consistently updated and running at optimal levels, free from inefficiencies
Internet Security

Internet security protects your organization and all its online interactions from malicious content on the web. While many aspects of IT security aim to protect your business from external cyber-attacks, internet security primarily concerns the safety of your employees, and how they interact with the internet.
Examples of internet security measures include:
- Security Awareness Training: arrange security awareness training to help employees identify and prevent online threats, such as unsafe downloads or connecting to unsecured networks
- Web Control and Filters: software that restricts what websites a user in your network can visit while browsing the internet, protecting them from hidden malicious code
Internet of Things (IoT) Security
Internet of Things (IoT) Security refers to the measures taken to protect internet-connected devices and the networks they operate on from cyber threats. These devices are commonly called IoT devices and can include anything from smart thermostats and cameras to industrial sensors and medical equipment.
Examples of IoT security strategies include:
- Network Segmentation: isolates IoT devices on a separate network to prevent unauthorized access to critical systems
- Firmware Updates: consistently updating device software to patch vulnerabilities and improve security
Top IT Security Threats to Businesses

Cybercriminals are more agile than ever. As new technologies and methods develop, your business must stay informed and proactive to defend against these evolving threats.
Below are some of the top IT security threats every organization should be aware of:
Malware
Malware is short for malicious software. This refers to programs designed to damage, disrupt, or gain unauthorized access to computer systems.
Common types of malware include:
- Viruses: malware that attaches to files and spreads when those files are opened, causing damage to data or systems
- Worms: self-replicating malware that spreads across an entire network, often carrying viruses or ransomware with it
- Trojan Horses: malware disguised as helpful or legitimate software to trick users into installing it
Ransomware
Ransomware is a type of malware that encrypts or locks victims’ data until a ransom is paid to the attacker. In 2024, over half of ransom demands (63%) were above $1 million2. These attacks affect businesses of all sizes and can put entire organizations out of business.
Examples of ransomware include:
- Encrypting Ransomware: encrypts files so they are inaccessible until the victim pays for a decryption key
- Locking Ransomware: locks users out of their devices until a ransom is paid
- Double Extortion Ransomware: threatens to leak stolen data unless a ransom is paid
Phishing

Phishing is one of the most common forms of cybercrime where criminals pretend to be a trusted entity and trick people into providing sensitive information, like passwords or credit card numbers.
Examples of phishing include:
- Fraudulent Emails: fake or spam emails that appear to be from legitimate sources, asking for personal information or linking to malicious websites
- Text Phishing (smishing): fraudulent texts that encourage recipients to click on bad links or share private information
- Phishing Websites: malicious websites with a name or domain that is similar to an official website
Third-Party Exposure
Hackers will often exploit vulnerable third-party software to bypass an organization’s security measures. This is known as third-party exposure.
For example, in 2024, vulnerabilities in a third-party cloud platform caused a large data breach for AT&T that allowed bad actors to illegally download call and text records of over 70 million customers.
Factors that make your business vulnerable to third-party exposure include:
- Using unvetted third-party applications
- Weak, shared, or repeated passwords and login credentials
- Partnering with vendors that don’t have strong IT security measures
Inadequate Data Management

Inadequate data management is like leaving a business unattended and the front door wide open. Without strong policies and safeguards, sensitive information becomes a sitting target for cyber threats.
The failure of a business to properly handle, store, secure, or manage its data can lead to data breaches, ransomware exploits, compliance violations, and more.
Poor Employee Cybersecurity Training
Even the most comprehensive IT security strategies can be rendered ineffective if employees lack the knowledge, skills, or awareness needed to recognize and respond to cyber threats effectively. Sometimes, all it takes is clicking on one bad link to put a company’s entire IT infrastructure at risk.
Cybersecurity training empowers your employees to recognize threats, follow safe cyber hygiene practices, and uplift the security of your entire business.
Why is IT Security for Businesses So Important?

No business is immune to cybersecurity risks. Companies of all sizes need a reliable strategy to mitigate external threats from cybercriminals and the potential for internal risks.
IT security helps protect your business, employees, and customers from cyberattacks like hacking and data breaches. This safeguards your company and its reputation and maintains customer trust.
Beyond protecting sensitive data and building trust with your customers, IT security is also necessary for regulatory compliance and avoiding costly downtime.
Regulatory Compliance
IT security helps businesses comply with industry regulations designed to protect sensitive data, such as:
- HIPAA (Health Insurance Portability and Accountability Act): for businesses in the healthcare industry, this act ensures that all patient health data remains confidential and secure
- GDPR (General Data Protection Regulation): mandates businesses to protect the personal data of individuals in the EU through proper handling, storage, and access controls
- PCI-DSS (Payment Card Industry Data Security Standard): security standards for handling online credit card transactions and protecting payment data
Remaining compliant and secure can help your business avoid potential fines or legal penalties.
IT Downtime is Expensive
Protecting your business from cyber threats also protects your finances. When systems go down, your business can’t make sales, process orders, or serve customers. These costs add up quickly.
In fact, recent studies show that downtime costs large organizations an average of $9,000 per minute3—and this doesn’t include the cost of getting things up and running again. Plus, this number also doesn’t account for the long-term cost of damaged brand reputation, compromised customer loyalty, and lost business.
By investing in IT security, businesses can protect their assets, ensure business continuity, and ultimately safeguard their reputation and financial stability.
Get a Free Consultation to Learn How IT Security Can Benefit Your Business
Cyber threats are more prevalent than ever, and they put you, your team, and your customers at risk. The best way to safeguard your business and your bottom line is to establish a proactive IT security plan before disaster strikes.
Don’t wait until it’s too late—claim your FREE consultation today to learn how IT security can benefit your Sonoma County business.
References
- Cost of a data breach 2024 | IBM. (n.d.). https://www.ibm.com/reports/data-breach
- Sophos. (2024). The state of ransomware 2024. In A Sophos Whitepaper. https://assets.sophos.com/X24WTUEQ/at/9brgj5n44hqvgsp5f5bqcps/sophos-state-of-ransomware-2024-wp.pdf
- Shepherd, D. (2024, March 18). Why DNS exploits continue to be a top attack vector in 2024. TahawulTech.com. https://www.tahawultech.com/insight/why-dns-exploits-continue-to-be-a-top-attack-vector-in-2024/



Comments